
CCNet
Feb 21, 2024 • 3 min read

The invisible threat: Vulnerabilities in software products
Vulnerabilities are not only ubiquitous in software products but also pose one of the greatest threats to cybersecurity. These invisible vulnerabilities often serve as the first entry points for cybercriminals to compromise systems and entire networks. Their significance cannot be underestimated as they provide the anonymity and flexibility attackers need for their remote operations.
A growing flood of new vulnerabilities
The latest IT situation report reveals an alarming trend: an average of 68 new vulnerabilities were reported daily, representing an increase of around 24% compared to the previous year. In total, almost 27,000 new vulnerabilities were identified over the year, affecting a wide range of software products – from specialized applications and complex server infrastructures to mobile apps.
The consequences of modularization
The increasing modularization and division of labor in software production have further exacerbated the threat landscape. A single vulnerability in a widely-used software component can potentially be exploited in a variety of applications, dramatically increasing the scope of a potential attack.
The criticality of vulnerabilities
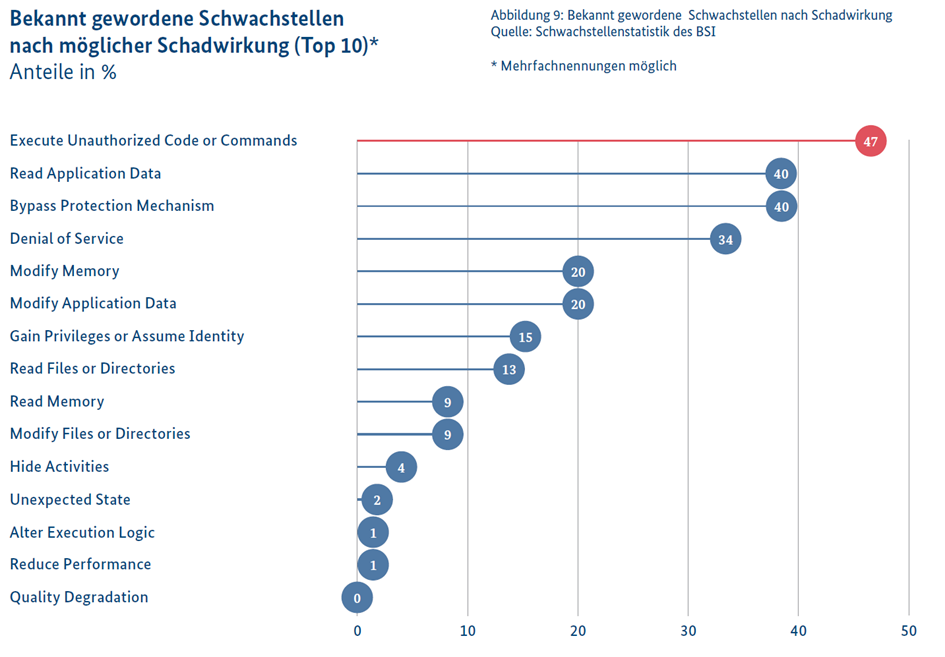
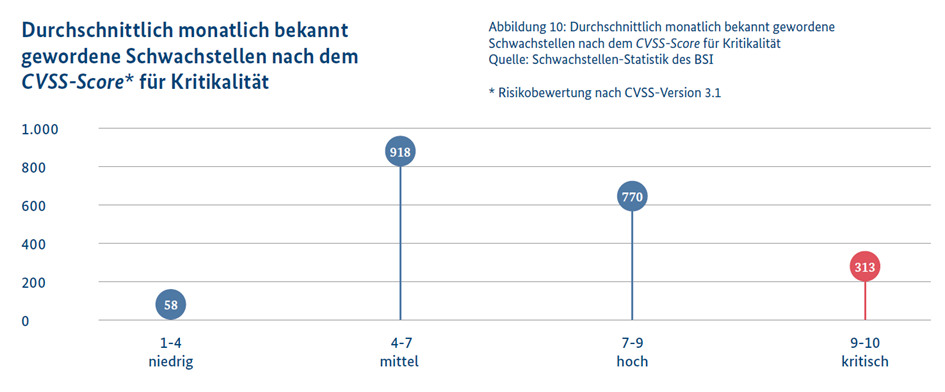
Vulnerabilities vary significantly in their criticality and the potential damages they can cause through their exploitation. To quantify the impact of these vulnerabilities, the Common Weakness Enumeration (CWE) is often used, while criticality is assessed through the Common Vulnerability Scoring System (CVSS). A considerable portion of vulnerabilities allows for the execution of unauthorized code or commands, facilitating, for example, the initial infection in a ransomware attack.
The threat posed by vulnerabilities
Approximately 47% of the vulnerabilities reported during the reporting period enabled attackers to bypass security measures, while about 40% allowed for data exfiltration. Such data can be used for cyber extortion or sold to other attackers. Additionally, every third vulnerability was exploitable for a Denial-of-Service (DoS) attack, underscoring the versatility and danger of these vulnerabilities.
The race for vulnerabilities
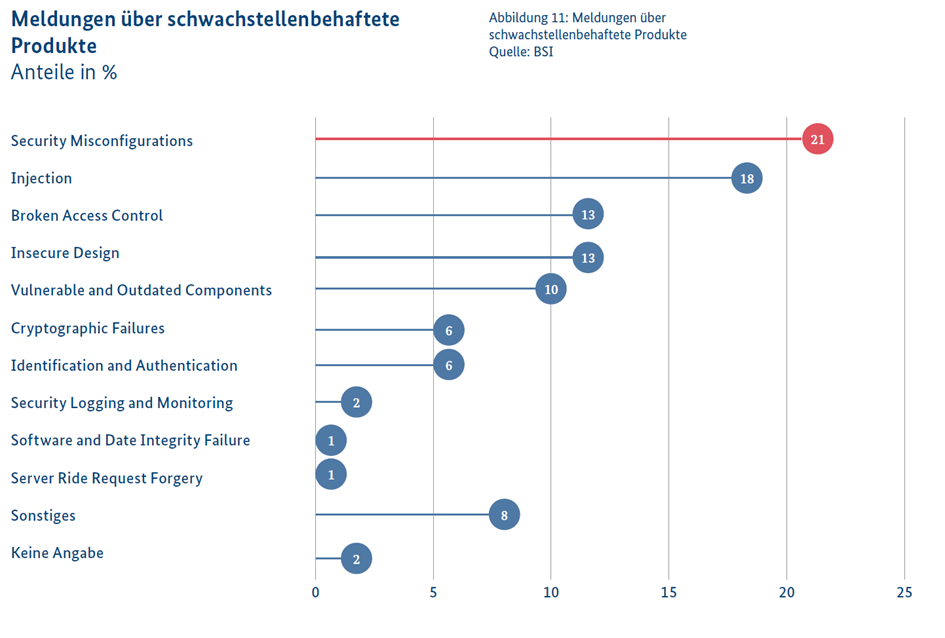
In the cyber realm, there is a constant race between security researchers and cybercriminals. Whoever discovers vulnerabilities first has the option: these can either be used to carry out cyberattacks, offered for sale in the darknet, or reported to manufacturers for remediation. The Federal Office for Information Security (BSI) plays a central role in this process, regularly receiving and classifying reports from security researchers.
Conclusion and outlook
The flood of newly discovered vulnerabilities presents a daily challenge for IT security professionals. The (partial) automation of processes in patch management, supported by standards like the Common Security Advisory Format (CSAF), offers potential to address this challenge. Through automation, vulnerability reports could be filtered more efficiently, and relevant reports for an organization identified more quickly.
Digitalization continues to advance, and new technologies emerge. It is essential that all stakeholders – from individuals and companies to governmental institutions – develop an awareness of the risks and take proactive measures to ensure the security of our digital world.
The increasing complexity and distribution of software products have heightened vulnerability to vulnerabilities. A comprehensive understanding of these vulnerabilities is critical to implementing effective countermeasures and reducing potential risks. Continuous monitoring and analysis of vulnerabilities enable companies to proactively respond to threats and close security gaps before they can be exploited. Additionally, close collaboration between security researchers, manufacturers, and regulatory authorities is essential for exchanging information and developing joint strategies.


