
CCNet
Feb 19, 2024 • 2 min read

Spam and Phishing: The Relentless Cyber Threats of the Digital Age
In the digital age, where communication and transactions are increasingly taking place online, spam and phishing have secured a permanent place in the arsenal of relentless cybercriminals. These unwanted and often harmful messages are more than just a nuisance; they pose a serious threat to the security and privacy of individuals and organizations. In this article, we will explore the mechanisms behind spam and phishing, the various methods of these attacks, and the growing role of Artificial Intelligence (AI) in their proliferation. Additionally, we will discuss effective strategies to mitigate these threats.
The Nature of Spam: More than Just Annoying Advertisements
Spam encompasses a broad spectrum of unwanted messages sent over the internet, typically via email. These can include harmless advertisements but also more dangerous content such as malware, fraudulent emails, and extortion attempts. Cybercriminals often use compromised servers, stolen email addresses, or even IoT devices to conduct their campaigns and create botnets. These botnets enable them to send spam in massive quantities, with the technology behind these attacks constantly evolving.
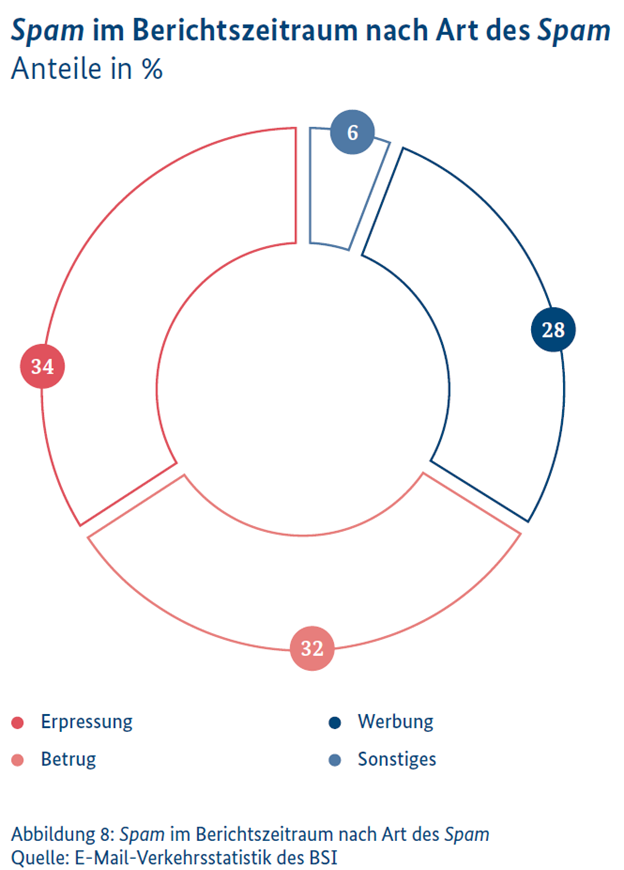
Phishing: The Art of Digital Deception
Phishing, a specific form of spam, aims to exploit personal and sensitive information from unsuspecting victims through social engineering. Cybercriminals pose as trustworthy entities to lure users into disclosing credentials or other valuable information. The creative use of smishing and vishing expands the arsenal of these fraudsters by extending traditional phishing attacks to SMS and voice calls.
The Evolution of Attack Methods
The IT Situation Report 2023 from BSI reveals alarming diversity in the methods and objectives of spam and phishing attacks. While some spam appears harmless, a significant portion conceals malicious intentions, including fraud and extortion. Complicating matters, phishing attacks are becoming increasingly sophisticated, particularly through the use of AI, enabling more authentic message construction and persuasive language imitation.
Current Trends: Exploiting Crisis Situations
Criminals adeptly exploit societal crises and major events to make their fraud attempts appear more credible. From phishing messages reacting to energy crises to fake donation appeals in the name of relief organizations, perpetrators demonstrate alarming flexibility in their methods. These campaigns play on people's fears and compassion to manipulate and deceive them.
The Impact of AI on Cyber Threats
The growing availability and advancement of AI technologies pose the risk of these tools being misused to make spam and phishing even more effective. AI can contribute to making phishing messages and websites nearly indistinguishable from legitimate ones, significantly increasing the risk of cyber attacks.
Prevention Strategies and Protective Measures
To defend against the constant threat of spam and phishing, it is crucial to stay informed about the latest security practices and take preventive measures. This includes user training, the deployment of spam filters, regular security updates, and the use of multi-factor authentication. Additionally, maintaining a critical attitude towards unexpected messages and always verifying the authenticity of requests is important.
Conclusion
Spam and phishing remain a significant challenge in the cyberspace. The constant evolution of these attacks requires continuous adaptation and refinement of security strategies. Through education, the use of advanced technologies such as Zero-Trust architectures, and the development of a critical online culture, we can hope to minimize these threats and make our digital world safer.


