CCNet
Feb 22, 2024 • 2 min read

Distributed Denial-of-Service Attacks: A Growing Cyber Threat
Denial-of-Service (DoS) attacks have become a growing ubiquitous threat to the availability of internet services. Even more concerning is the rise of Distributed Denial-of-Service (DDoS) attacks, where multiple systems are coordinated to cripple websites and internet services. These attacks inundate web servers with requests until the services collapse under the load and become inaccessible.
The Mechanics Behind DDoS Attacks
DDoS attacks are feared not only for their ability to temporarily render services unavailable but also for their versatility. They can be executed by individuals or groups with motivations ranging from simple vandalism to more complex goals such as extortion or political activism. In some cases, DDoS attacks are even employed to distract from other, more sophisticated cyber threats, such as ransomware or Advanced Persistent Threats (APTs).
Objectives and Consequences of DDoS Attacks
The objectives of DDoS attacks are diverse. Besides directly extorting victims for financial gain to halt the attacks, some attackers use this technique to harm competitors or convey political messages. The consequences of such attacks vary from financial losses for online retailers unable to operate during an attack to reputational damage and a loss of trust in critical services when, for instance, banks or law enforcement agencies are affected.
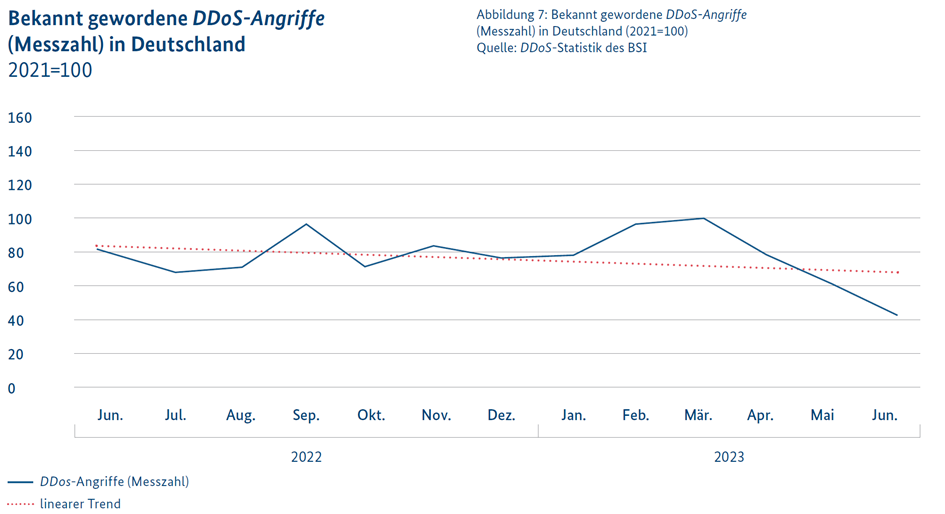
Measurement and Trends of DDoS Attacks
The number of reported DDoS attacks in Germany can be measured through a specific index. An example is an index value of 95 points in February 2023, indicating that the number of DDoS attacks in that month corresponded to 95% of the 2021 annual average. Particularly noteworthy is the decline in DDoS activities compared to earlier periods, suggesting more effective combatting and prevention of these attacks. Initial projections in Q1 of 2024, however, show a renewed increase to approximately 105%.
The Impact of Hacktivism
In the context of ongoing conflicts, DDoS attacks have been utilized as a tool for politically motivated hacktivism. These attacks aimed to sow societal unrest and undermine confidence in the state's ability to protect and provide for the population. Although such attacks typically cause minimal material damage, their ability to garner public attention and convey political messages should not be underestimated.
Conclusion
DDoS attacks pose a significant threat to the security and availability of online services. While the motivations behind these attacks may vary, the potential extent of damage, especially concerning societal unrest and loss of trust, is considerable. Developing strategies for the mitigation and prevention of DDoS attacks remains a central challenge for cybersecurity experts, governments, and businesses worldwide. It is crucial for all stakeholders to collaborate in enhancing resilience against these and other cyber threats.