CCNet
Feb 7, 2024 • 2 min read

The Urgency of Zero Trust Architecture (ZTA) in the Industrial Sector: Insights from the IT Threat Report Germany 2023
The cyber threat landscape is evolving rapidly and poses new challenges for the industrial sector. The IT Situation Report Germany 2023, published by the Federal Office for Information Security (BSI), not only presents the current threat situation, but also emphasizes the need for a robust security strategy such as the Zero Trust Architecture (ZTA).
Statistical overview: An alarming picture
The report highlights the tense to critical threat situation in cyberspace. The average daily growth in new malware variants is particularly striking. In 2022, this average was an impressive 280 to 304 new variants per day, underlining the need for continuous vigilance and adaptive security strategies.
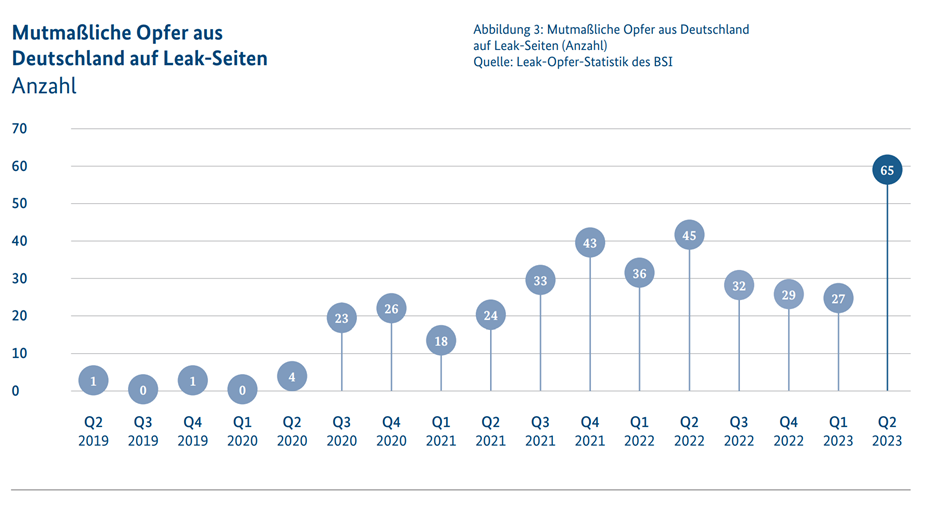
SMEs in the focus of cyber criminals
Small and medium-sized enterprises (SMEs) as well as local authorities and municipal businesses are increasingly being targeted by cyber criminals. This indicates a targeted approach against easily vulnerable targets, where the focus is no longer on maximizing the potential ransom, but on rational cost-benefit calculations.
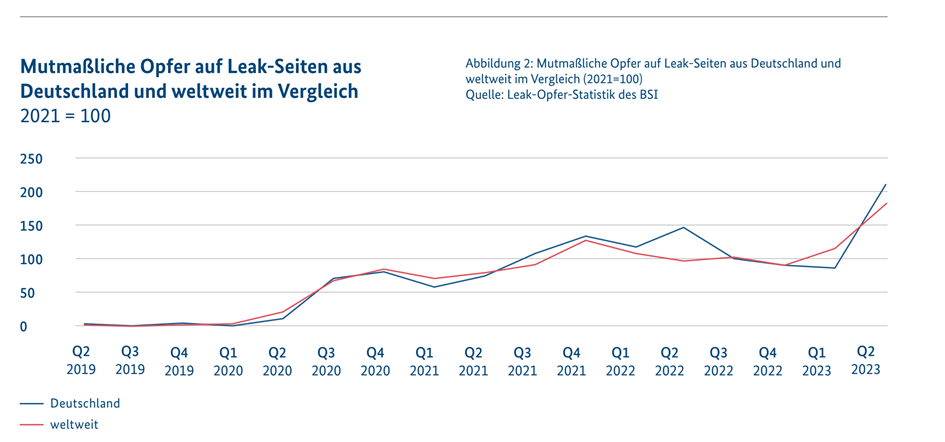
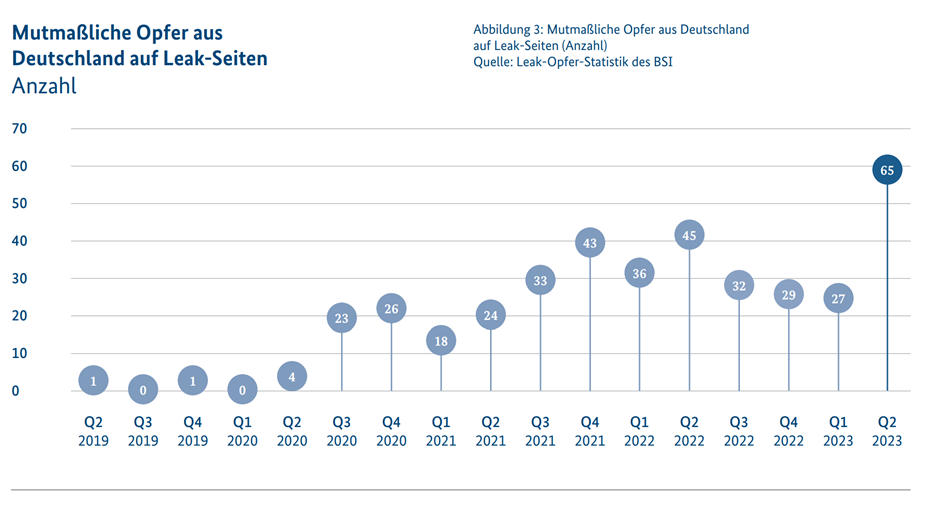
Advanced Persistent Threats and vulnerabilities
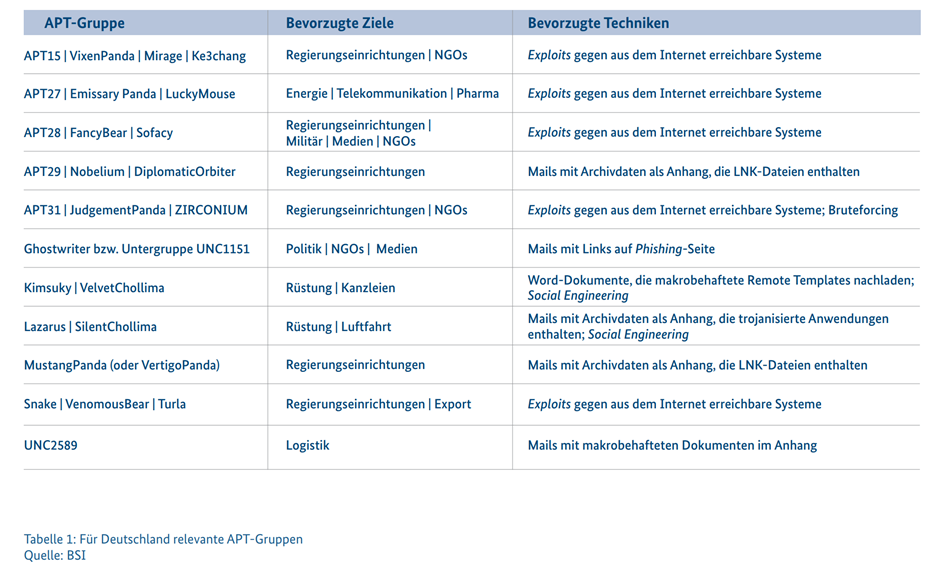
Advanced Persistent Threats (APTs) are aimed at gathering information and are increasingly targeting critical infrastructure and government institutions. Added to this is the worrying increase in vulnerabilities in software products, with almost 70 new vulnerabilities being discovered every day, of which around 15% are classified as critical.
Why Zero Trust Architecture (ZTA) is indispensable
Zero Trust Architecture (ZTA) offers a dynamic and holistic approach to securing networks and data. Its principles are critical to responding to complex and ever-changing threats:
- Micro-segmentation: ZTA enables fine-grained control of network access, severely limiting attackers' freedom of movement.
- Dynamic access controls: Continuous review of access rights ensures flexible and secure operations.
- Increased resilience against ransomware and APTs: ZTA principles can minimize the impact of ransomware attacks and ensure better protection against APTs.
Insights and Conclusions
The IT Situation Report Germany 2023 underlines the urgency of an adaptive and robust security strategy for companies, especially SMEs and critical infrastructures. Zero Trust Architecture provides a future-proof framework to strengthen resilience and security in the digital age. At a time when cyber threats are becoming increasingly complex, the implementation of ZTA in the industrial sector is essential to both prevent attacks and minimize their potential impact.