CCNet
Feb 14, 2024 • 2 min read

The Advancing Threat of Ransomware: A Look into the Cybercriminal Underground Economy and Extortion Tactics
In the realm of cybercrime, ransomware stands out as one of the most persistent, advancing and damaging threats. This article takes a look on two core aspects of the ransomware threat: the increasing complexity of the cybercriminal underground economy and the sophisticated extortion tactics employed against small and medium-sized businesses (SMBs), as well as educational and local government institutions.
The Cybercriminal Underground Economy
Cybercrime has evolved into a highly organized underground economy that offers services and tools for every stage of a ransomware attack. This evolution has significantly enhanced the efficiency of attacks. Attackers can now access a wide range of services, from the provision of the necessary ransomware to assistance in ransom negotiations. The specialization within this underground economy allows providers to continuously refine and improve their tools, thereby increasing the threat to potential victims.
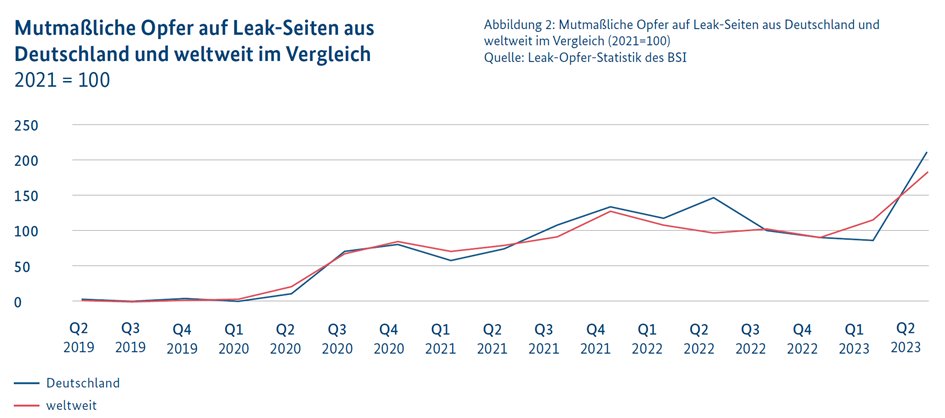
These services are often offered on a commission-based structure, where the so-called affiliates who carry out the attacks pay a portion of the extorted ransoms to the providers of the services used. This structure not only encourages efficient division of labor among cybercriminals but also accelerates the dissemination of advanced attack tools.
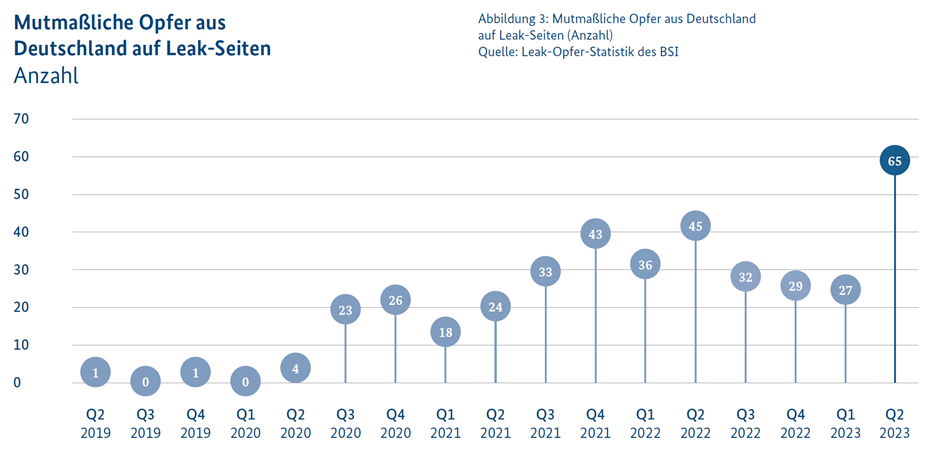
Ransomware Extortion and Its Targets
Recently, a clear trend has emerged: cybercriminals are increasingly targeting entities they perceive as vulnerable. Maximizing potential ransom is no longer the primary objective; instead, attackers are focusing on the cost-benefit ratio of their operations. This has led to a rise in ransomware attacks on small and medium-sized enterprises (SMEs), state and local government agencies, as well as educational institutions.
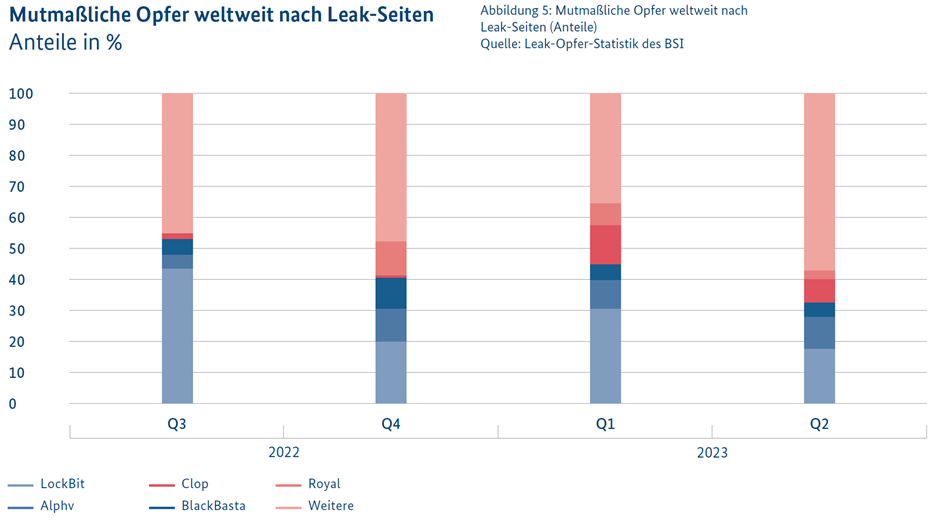
This development underscores the need for increased cyber resilience. Organizations and institutions must take preventative measures to protect themselves against these types of cyber attacks. These include implementing robust security policies, conducting regular security audits and assessments, and training employees on the risks and signs of phishing attacks and other entry points for ransomware.
Conclusion
The evolution of the cybercriminal underground economy and the targeted selection of victims by cybercriminals highlight that the threat from ransomware is becoming more layered and dynamic. The increasing professionalization of cyber attacks requires an equally dynamic and proactive approach to cyber resilience. Small and medium-sized enterprises (SMEs), educational and administrative institutions must be aware of this growing threat and implement appropriate security measures to protect their data and systems. Developing a comprehensive cyber defense strategy that includes both preventive and reactive components is essential in today's digital era.